Volume License
Finance - Consultancy - MSSP
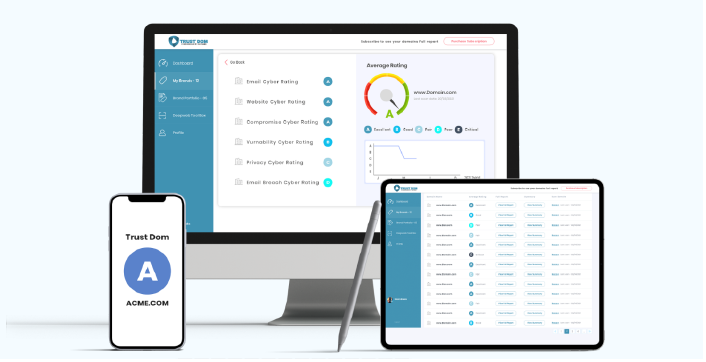
Volume Licenses
There are three Volume Licenses offered by Cygienic: Cyber Essentials 360, Cyber Essentials Lite, and Self-Service. Contact our Cygienic sales team to discuss our partnership options for Insurance, Private Equity, M&A, Venture Capitalists, Auditors, MSSP, and Cyber consultancy.
We offer a comprehensive suite of cyber risk assessments, managed services, and high-volume, low-cost cyber risk service licenses.
Cyber Essentials 360 License
Cyber Essentials 360 offers a specialized cybersecurity risk assessment service tailored for volume workflow. It is designed to evaluate business investments and contribute to the valuation process for both existing and prospective company portfolios
The service offers a unique cyber risk assessment program, comprising eight steps designed to deeply evaluate your portfolio of companies’ cyber risks, threats, and exposure.
Cyber Essentials Lite License
Cyber Essentials Lite is crafted to facilitate a streamlined risk assessment for businesses. Leveraging our exclusive Attack Surface Data, Compliance Risk Surveys, and Financial Quantification Calculators, services can obtain quantifiable data to reinforce company risk. This is an efficient, expedited, and cost-effective service for high-volume services.
Self-Service License
The Self-Service license offers a true self-service experience. Cygienic will guide you through onboarding and supply the system with credits, allowing you to organize and oversee your own risk assessments. The onboarding process is swift, typically completed within a few hours, and support is available for any system-related issues.
Cyber Essentials 360 & Lite Risk Assessments
Cyber Profile -01 The initial step in the cyber essential journey is to identify the company's risk profile, which serves as a gauge for the company's cyber maturity, and as a preliminary phase in guiding a company towards the appropriate cyber framework. This phase relies on a guided self-assessment, followed by a remote sample audit and a final compliance rating and grade.
Attack Surface -02 (Lite) The Attack Surface is a non-intrusive cybersecurity assessment of a company’s internet-facing web servers - web applications, websites, and email systems. This assessment examines the security settings and potential vulnerabilities within these systems, yielding a -comprehensive cybersecurity rating and remediation recommendation.
3rd-Party Risk - 03 This is an assessment of the critical supply chain and your essential business partners. This can be conducted as a non-intrusive attack surface assessment; or as a deep dive-risk compliance assessment survey.
Threat Analysis- 04 The profile of cyber adversaries targeting your industry - and their attack vectors will be analyzed and recorded against your existing cyber defense controls. In addition, our security analysts will search the Darknet to find company assets for sale or simply shared and posted on bulletins e.g. user passwords, company web-assets, or confidential documents.
Vulnerability Scan & Email Phishing - 05 Using industry-standard vulnerability tools, our consultants will target your company’s internet services e.g. email and websites to identify known vulnerabilities. You will be provided with a technical report inclusive of any improvement recommendations. Our security analysts will also conduct an email campaign to entice users to click on links or attachments to test the company’s vulnerability to phishing.
Financial Risk Quantification - 06 (Lite) Conducting a financial impact analysis involves employing risk quantification modeling to assess the potential consequences of a company's cyber-attack, system breach, data breach, or ransomware, along with calculating the likelihood of such events. This process enables improved budgeting and strategic planning for cybersecurity risks and valuation.
Policy and Control Recommendation - 07 A policy and controls report is a high-level recommendation for framework controls and policies (inclusive of policy, guides, and security awareness samples) The report is supported by the output from previous stages.
Cyber Essentials Reports - 08 A concise overview of the Cyber Essential 360 stages is presented in this executive summary report, facilitating clear comprehension and suitable for board-level presentations to support the company's risks. Furthermore, a comprehensive report covering all Cyber Essential 360 stages is also incorporated.
For more details on our Financial Services Licenses please contact sales@cygienic.com