Cyber Prevention Management
...Powered by Cygienic Cybershield
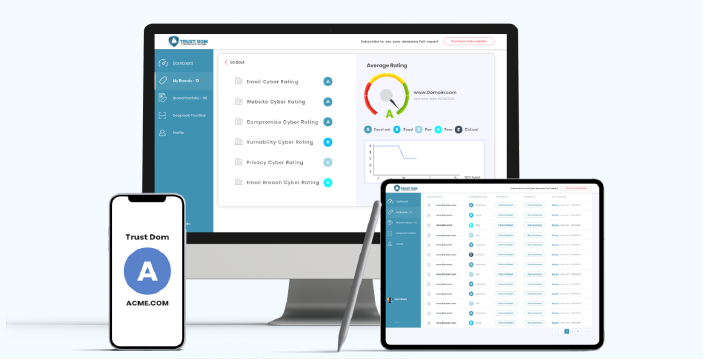
Cyber Prevention Management refers to identifying, assessing, and analyzing the vulnerabilities and potential entry points that malicious actors could exploit to gain unauthorized access to an organization's data and systems. It involves identifying and mapping all the components and assets that makeup an organization's infrastructure, such as a company's website, email server, web applications, and more.
Cyber Prevention Scope |
|
|
|
|
|
|
A non-intrusive cybersecurity assessment of your company's internet-facing assets, including web servers, applications, websites, and email systems. This evaluation reviews security settings and identifies potential vulnerabilities, providing a comprehensive cybersecurity rating and remediation recommendations.
The attack surface scanner is an algorithmic generative technology, which provides a detailed analysis of any company's cybersecurity risk profile. All told, there are 55 cybersecurity controls assessed, all of which are passive and non-intrusive to any company's defense technologies. In essence, the scan probes for cybersecurity weak points, without being detected, or attempting to break in and then takes the results to calculate a risk profile and a remediation plan.
From industry regulations and standard questionnaires to security policies and awareness material, the platform has everything pre-built and centrally managed for you.
Industry-standard tools scan your company systems for vulnerabilities, search the darkweb for company confidential data leaks, and check if company systems have been compromised.
Our Malware Tracker Service is included with our standard Cygienic Subscription. This service provides continuous scans of your registered assets to identify Remote Access Trojans (RATs) and Command and Control (C&C) botnets. You will be promptly alerted via phone calls, email, and WhatsApp if any malware is discovered
Executive summary reports designed for board-level presentations, facilitating a clear understanding of the company's risk profile. Receive a high-level recommendation report for framework controls and policies, including policy documents, tech guides, playbooks, and security awareness training samples, supported by insights from previous stages.
The Cygienic third-party risk management offers a comprehensive set of cybersecurity risk assessment programmes to help you manage and monitor your supply chain risks. With our cutting-edge technology, we can help identify and address potential vendor cyber risks.
Contact sales@cygienic.com to discuss our Cygienic Cybershield ™