Cygienic Cybershield+
Insurance Protection + Cyber Prevention
Approximately 60% of small and medium-sized enterprises (SMEs) close within six months of a significant cyberattack. This alarming statistic highlights the devastating impact of cyber incidents on smaller businesses, which often lack the resources to recover from financial, reputational, and operational damages caused by these attacks.
Factors contributing to closure include:
Investing in proactive cybersecurity measures, such as training, robust cyber insurance, and recovery plans, is critical to mitigate these risks.
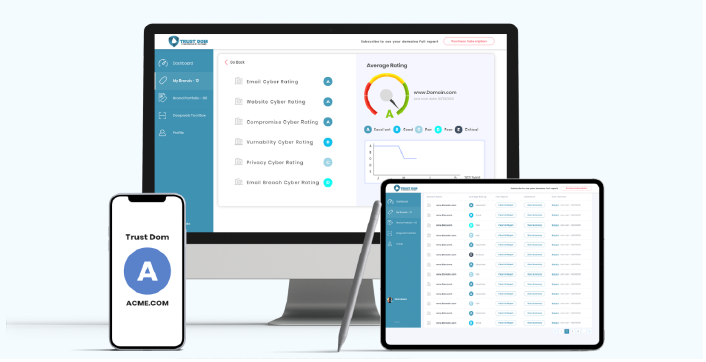
Cybershield+ is a proactive form of cyber insurance that provides coverage in the event of a cyber incident and includes preventative measures and real-time responses to threats. This type of insurance partnership leverages Cygienic’s advanced technologies such as continuous monitoring, and response to help organizations detect and mitigate cyber risks before they escalate into significant incidents.
As your dedicated cybersecurity risk partner, we support the entire lifecycle of the cyber insurance policy, from inception to renewal. We take care of all your cyber risk & hygiene assessments, underwriter interactions, client monitoring, and support on incident response.
With our service, clients are offered a 365-day fully managed cyber risk management and monitoring service, and regular cyber risk reports.
By offering our cyber services, we aim to reduce the frequency and severity of cyber claims, ultimately benefiting insurers and policyholders. This is especially advantageous for small and medium-sized enterprises (SMEs) and Startups that may lack the resources to implement robust cybersecurity measures on their own.
The lifecycle of your cyber insurance involves several critical stages, from initial assessments and right-sizing your coverage to renewals, incident response, and claims management. Throughout this entire process, Cygienic Insurance experts will be your trusted partners, guiding you every step of the way to ensure comprehensive protection and seamless support.
Employ risk quantification modeling to analyze the potential financial consequences of cyber incidents, such as attacks, breaches, or ransomware. This analysis aids in budgeting and strategic planning for cybersecurity risks.
This provides a comprehensive, simple measurement of the potential risk versus the return on investment. From calculating cyber insurance premiums to the cost of data breaches and ransomware, it can build your financial risk profile, allowing you to make more informed cybersecurity investment choices. Why wait to calculate an event cost, especially when you can financially mitigate a future event, today!
Cyber Prevention Management refers to identifying, assessing, and analyzing the vulnerabilities and potential entry points that malicious actors could exploit to gain unauthorized access to an organization's data and systems. It involves identifying and mapping all the components and assets that makeup an organization's infrastructure, such as a company's website, email server, web applications, and more.
|
|
|
|
|
|
|
|
Cyber Attack Surface Management
A non-intrusive cybersecurity assessment of your company's internet-facing assets, including web servers, applications, websites, and email systems. This evaluation reviews security settings and identifies potential vulnerabilities, providing a comprehensive cybersecurity rating and remediation recommendations.
Security Compliance Management
From industry regulations and standard questionnaires to security policies and awareness material, the platform has everything pre-built and centrally managed for you.
Vulnerability & Data Threat Intelligence
Industry-standard tools scan your company systems for vulnerabilities, search the darkweb for company confidential data leaks, and check if company systems have been compromised.
Malware Tracker Management
Our Malware Tracker Service is included with our standard Cygienic Subscription. This service provides continuous scans of your registered assets to identify Remote Access Trojans (RATs) and Command and Control (C&C) botnets. You will be promptly alerted via phone calls, email, and WhatsApp if any malware is discovered
Automation, Workflow & Reporting
Executive summary reports designed for board-level presentations, facilitating a clear understanding of the company's risk profile. Receive a high-level recommendation report for framework controls and policies, including policy documents, tech guides, playbooks, and security awareness training samples, supported by insights from previous stages.
The Cygienic third-party risk management offers a comprehensive set of cybersecurity risk assessment programmes to help you manage and monitor your supply chain risks. With our cutting-edge technology, we can help identify and address potential vendor cyber risks.
Contact sales@cygienic.com for Cygienic Cybershield+