Broker Managed Service
Powered by Cygienic Cyber Underwriter
Insure - Secure - Monitor
Cygienic offers a turnkey, white-label solution that enables Insurance Brokers, Agents, Insurers, and MGAs to enter the cyber insurance market with speed and confidence—no need for in-house cyber underwriters, insurtech platforms, or cybersecurity teams.
Powered by our Cyber Underwriter™ platform, the service includes cyber risk assessments, real-time monitoring, and expert insurance advisory—ensuring your clients receive the right level of cyber risk evaluation to secure effective coverage and build cyber resilience. As your dedicated cybersecurity risk partner, we support the entire lifecycle of the cyber insurance policy, from inception to renewal. We take care of all your cyber risk & hygiene assessments, underwriter interactions, client monitoring, and support on incident response.
Q1. What is the cost for Broker Managed Service?
Just $250 per month (50% discount paid annually), with the first month free.
Q2. What does the fee cover?
Q3. Is there a fee for each cyber insurance assessment?
No. You have unlimited assessments conducted by Cygienic Brokers.
Q4. Can we only start paying when we get our first cyber insurance premium?
Yes. We wont charge you until we get you your first cyber insurance premium.
Q5. Who retains the client's cyber insurance premium commission?
You do—we submit the insurance request under your company name to the insurer, and therefore you get to keep 100% of the premium commission.
Q6. What’s included in the cyber assessment?
We evaluate the client's attack surface, internal control compliance, and financial risk exposure. We also submit a request to the insurer and provide you with a high-level cyber risk report.
Q7. What's the financial opportunity here?
This is a $64 billion insurance market in its infancy, particularly within the SME market.
Q8. What additional services are available?
We offer full cybersecurity managed services, including 24/7 system monitoring. These services are quoted separately.
Q9. Can we earn commission from other cyber services sold to clients?
Yes. You will be commissioned for any cybersecurity services we resell to your clients. This will range from 10% to 30% commissions
Q10. Do you offer white-label services?
Yes. All client reports can be branded with your company’s logo and identity.
Q11. Do you offer lite managed cybersecurity services?
Yes. We can deliver a simplified, branded monthly report that includes attack surface monitoring and basic risk management reports.
Q12. Do you provide bespoke cyber risk assessments?
Yes. We offer tailored services such as third-party risk assessments, in-depth cyber risk reviews, vulnerability management, threat intelligence monitoring, and more.
Q13. Can the client also access Cygienic's Cyber Underwriter™?
Yes. We offer your client licenses to access their own cyber risk data - there are 2 options: Underwriter Client ($10 per month) or Underwriter Admin ($250 per month).
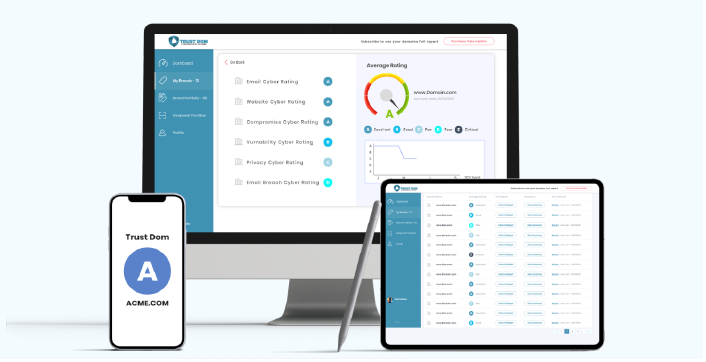
Cygienic’s Cyber Underwriter Services equips brokers, agents, insurers and MGAs with data-driven insights to streamline cyber risk assessments. By automating security evaluations and integrating with insureds’ environments, it delivers actionable reports that support faster, more accurate underwriting. The service helps identify key exposures and improves risk pricing confidence.
The lifecycle of your cyber insurance involves several critical stages, from initial assessments and right-sizing your coverage to renewals, incident response, and claims management. Throughout this entire process, Cygienic Cyber Consultancy experts will be your trusted partner, guiding you every step of the way to ensure comprehensive protection and seamless support. We can help you reduce client premiums and identify where the likelihood of an insurance claim may arise.
We will support and calculate the business exposure based on:
Powered by our Cyber Underwriter™ platform and SOC centre, we identify, assess, and analyze vulnerabilities and potential entry points that malicious actors could exploit to gain unauthorized access to an organization's data and systems. Cygienic enables comprehensive mapping of all infrastructure components and assets, such as websites, email servers, and web applications.
We also monitor your endpoints and servers with our SIEM and XDR agents. You get a complete 360 degree monitoring service of the inside and outside of your company.
Our Malware Tracker Service is included with our standard Cygienic Subscription. This service provides continuous scans of your registered assets to identify Remote Access Trojans (RATs) and Command and Control (C&C) botnets. You will be promptly alerted via phone calls, email, and WhatsApp if any malware is discovered
Contact sales@cygienic.com or let's schedule a call